OVAL Language Overview
The OVAL Language standardizes the three main steps of the assessment process: representing configuration information of systems for testing; analyzing the system for the presence of the specified machine state (vulnerability, configuration, patch state, etc.); and reporting the results of this assessment.
OVAL Language Benefits
- A simple and straightforward approach for determining if a software vulnerability, configuration issue, program, or patch exists on a given system.
- Standard Extensible Markup Language (XML) schemas that outline the necessary security-relevant configuration information.
- A single XML document that encodes the precise details of specific issue.
- An open alternative to closed, proprietary, and replicated efforts.
- Supported by a community of security experts, system administrators, and software developers
- Industry-endorsed via the OVAL Board and OVAL Developers Forum.
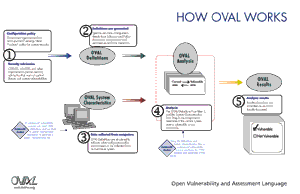
How OVAL Works
The OVAL Language involves three main categories:
- OVAL System Characteristics schema for collecting configuration data from systems for testing.
- OVAL Definition schema for testing the presence of a specific machine state (vulnerable, compliance, etc.).
- OVAL Results schema for reporting the results from the evaluated systems.
Collecting Information from Systems
The OVAL System Characteristics schema defines a standard XML format for representing system configuration information, which includes operating system parameters, installed software application settings, and other security relevant configuration values. The schema provides a "database" of system characteristics against which OVAL definitions can be compared in order to analyze a system for the presence of a particular machine state. The schema can also be used as an exchange format that can be incorporated into a variety of tools. By utilizing the provided OVAL System Characteristics file, other applications would not need to perform data collection, but rather can use the provided information to perform analysis. MITRE’s reference OVAL Interpreter is an example of an application that generates data in the OVAL System Characteristics schema format and makes it available to these other applications. Other information security products and services that incorporate the OVAL System Characteristics schema are listed in the OVAL Adoption Program section.
Standardized Tests
The OVAL Definition schema is the language framework for writing OVAL Definitions in XML. OVAL Definitions encode the details of a specific machine state (when is a system vulnerable, in compliance, etc.) enabling testing of a system to be automated. The OVAL Language’s standardized schemas also allow a wide range of computer security professionals to discuss the technical details of determining whether a vulnerability is present on a system, whether the configuration settings of a system meets a security policy, and/or whether a patch is present on a system.
There are two parts to the schema for writing OVAL Definitions, a core schema that describes the basics of the format, and individual component schemas for tests that are specific for individual OS platforms or applications. For example, there is a UNIX schema containing tests written for UNIX platforms, and a Windows schema for tests written for Windows platforms.
MITRE’s reference OVAL Interpreter is an example of an application that interprets OVAL definitions written against the OVAL Definition schema. Other information security products and services that incorporate OVAL definitions are listed in the OVAL Adoption Program section.
Results of the Tests
The OVAL Results schema defines a standard XML format for reporting the results of an evaluation of a system. The results data contains the current state of a system’s configuration as compared against a set of OVAL Definitions. The OVAL Results schema allows applications to consume this data, interpret it, and take the necessary actions to mitigate the vulnerabilities and configuration conflicts. For example, installing patches, altering system configuration settings, and/or taking external precautions to limit access to the affected systems. This schema also defines a standard exchange format that can be incorporated into a variety of tools. MITRE’s reference OVAL Interpreter is an example of an application that generates data in the OVAL Results schema format, and makes it available to other applications. Other information security products and services that incorporate the OVAL Results schema are listed in the OVAL Adoption Program section.
Additional Information
For additional information about the OVAL Language see Structure of the Language, Use Cases, and Versioning. For the current version of OVAL see the Releases page.
Page Last Updated: April 28, 2015